But what I did on windows using Putty was to feed my OpenSSH private key to putty-gen and generate a private key in PPK format. However, I would be creating a bash script from server 1 that will execute some commands on server 2 via SSH. Jul 22, 2015 Select SSH-2 RSA and enter 2048 for bits. Enter a comment for your key pair and click Generate. You will be asked to move the mouse around to generate some entropy. Once the key is done you can select it and paste it into the switch. Nov 23, 2011 Solved: Hi, i have a switch 2960 24TC-L with c2960-lanbasek9-mz.150-1.SE.bin and SSH v1 enabled. When i try to enable SSH v2 the swith tell me that i have to create a crypto key rsa. I generated the crypto key rsa with 1024 bits and when i try to.
Now we can generate the RSA keypair: R1(config)# crypto key generate rsa The name for the keys will be: R1.NETWORKLESSONS.LOCAL Choose the size of the key modulus in the range of 360 to 4096 for your General Purpose Keys. Aug 22, 2013. Aug 31, 2019 SSH authentication on Cisco NX-OS devices provide X.509 digital certificate support for host authentication. An X.509 digital certificate is a data item that.
Q: I have a Cisco switch in my network, which I can access by hooking up a console cable directly to the device. I like to access the switch remotely using SSH. How can I enable ssh on my Cisco 3750 Catalyst Switch?
A: By default, when you configure a Cisco device, you have to use the console cable and connect directly to the system to access it. Follow the steps mentioned below, which will enable SSH access to your Cisco devices. Once you enable SSH, you can access it remotely using PuTTY or any other SSH client.
1. Setup Management IP
First, make sure you have performed basic network configurations on your switch. For example, assign default gateway, assign management ip-address, etc. If this is already done, skip to the next step.
In the following example, the management ip address is set as 192.168.101.2 in the 101 VLAN. The default gateway points to the firewall, which is 192.168.101.1
2. Set hostname and domain-name
Next, make sure the switch has a hostname and domain-name set properly.
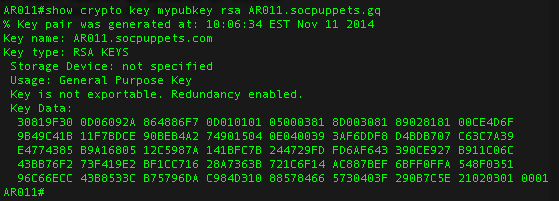
3. Generate the RSA Keys
The switch or router should have RSA keys that it will use during the SSH process. So, generate these using crypto command as shown below.
Also, if you are running on an older Cisco IOS image, it is highly recommended that you upgrade to latest Cisco IOS.
4. Setup the Line VTY configurations
Setup the following line vty configuration parameters, where input transport is set to SSH. Set the login to local, and password to 7.
If you have not set the console line yet, set it to the following values.
5. Create the username password
If you don’t have an username created already, do it as shown below.
Note: If you don’t have the enable password setup properly, do it now.
Make sure the password-encryption service is turned-on, which will encrypt the password, and when you do “sh run”, you’ll seee only the encrypted password and not clear-text password.
5. Verify SSH access
From the switch, if you do ‘sh ip ssh’, it will confirm that the SSH is enabled on this cisco device.
/x-plane-10-key-generator.html. After the above configurations, login from a remote machine to verify that you can ssh to this cisco switch.
In this example, 192.168.101.2 is the management ip-address of the switch.
If you enjoyed this article, you might also like.
Using Rsa Keys Generated From Switch Windows 10
Using Rsa Keys Generated From Switch On Computer
Next post: How to Backup Oracle Database using RMAN (with Examples)
Using Rsa Keys Generated From Switch Location
Previous post: How to Use C++ Single and Multiple Inheritance with an Example